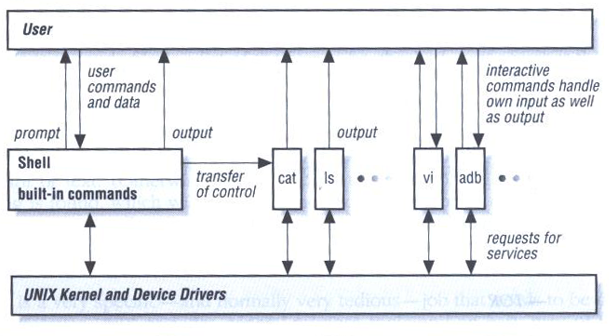
System Tables…
- Whenever definition change occurs those activities will be recorded in the database.
- Those information are kept in tables known as system tables.
- Similar to the tables we created earlier but this will maintain only by the database itself.
- No user intervention is needed.
- This type of data is called meta data.
Schemas…
- Used to group database objects such as tables, views, stored procedures, etc
- Can be created using CREATE SCHEMA statement
Example…
- Create an academic schema and allow it access to the user, AccDiv
- CREATE SCHEMA Academic AUTHORIZATION AccDiv
- Then create the table Modules in this schema
- The name given to a table must be unique within the schema
- Same object name can be created in another schema
- DROP SCHEMA Academic
Catalogs…
- A catalog is a named group of schemas.
- Virtual one.
- There is no CREATE CATALOG statement.
- Each catalog should contain a schema called INFORMATION_SCHEMA which defines no.of views for system tables.
- INFORMATION_SCHEMA.TABLES
- INFORMATION_SCHEMA.COLUMNS
.png)
.png)